CatDV Web Access via a DMZ
This page describes how to configure secure public web access to CatDV Server using a DMZ-based deployment. Internet security is a wide topic and it is strongly recommended that customers seek professional internet security advice to ensure their security arrangements are appropriate. Organisations wishing to provide public Internet access to their systems commonly make use of a DMZ (De-Militarized Zone) network architecture to reduce the risk of attacks. Only servers in the DMZ are accessible from the public Internet, and these machines can be locked down to provide a single, or very small number, or defined services, so reducing their attack surface. The internal firewall, between the DMZ and the internal network, is configured to only allow very specific traffic from these machines. A typical CatDV Server installation, running in a DMZ environment, is shown below: This installation contains a number of components:
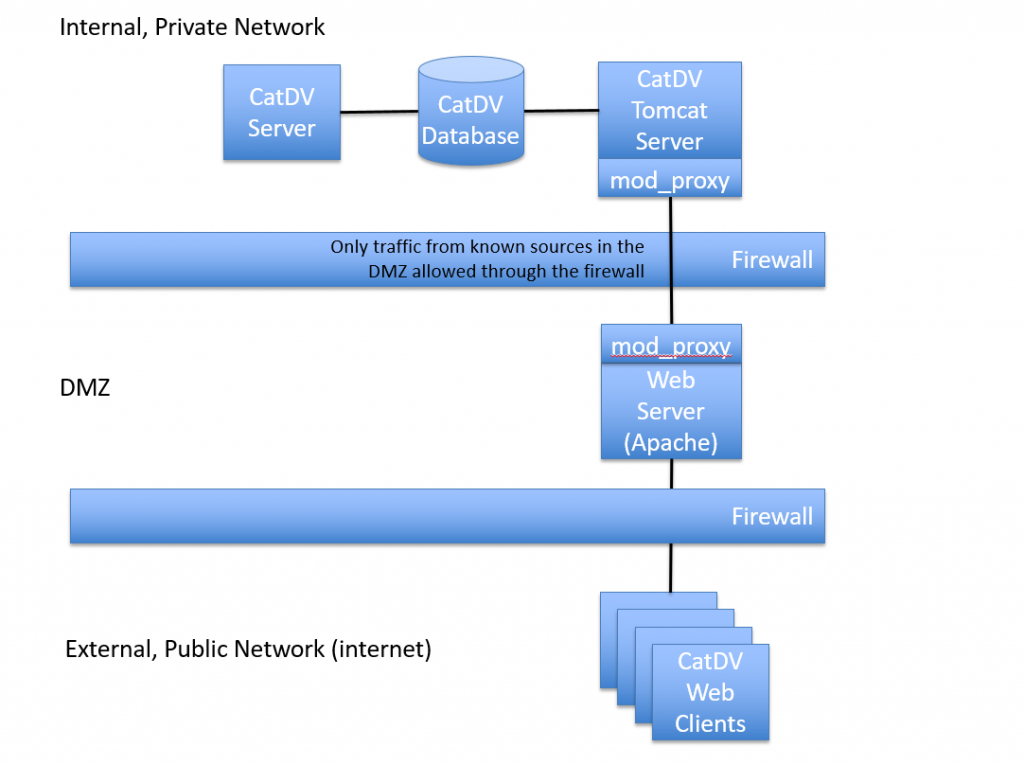
1. CatDV Server itself running on an internal server
2. A web server, running in the DMZ, with just Apache running on it. No application software is installed on this server
3. HTTP_proxy – the Apache-Tomcat connection technology configured on the DMZ machine
4. Appropriate firewall rules to control traffic between the web servers typically port 80 or 443
1. CatDV Server
If SETTING UP A PROXY FOR THE FIRST TIME, NO CONFIGURATION OF THE CATDV SERVER IS NEEDED WHEN USING HTTP_PROXY
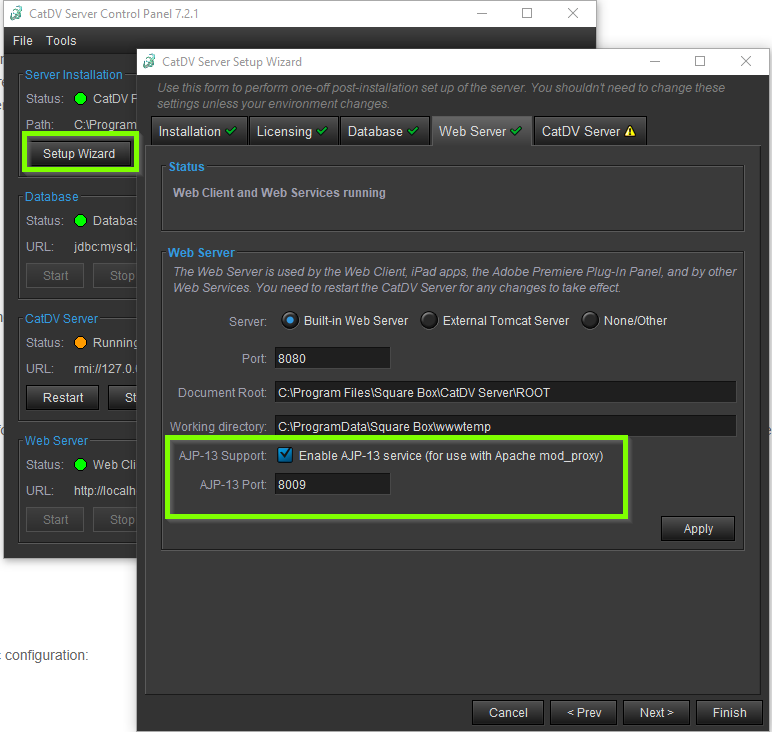
If you are using our legacy mod_proxy Please disable the AJP13 protocol on the CatDV server in the Web Server Section of the Catdv Server Setup wizard
2. Web Server in the DMZ
Apache is an industry standard web server and there are many online guides for how to install and configure Apache. Installation instructions and downloads are available here.
3. Apache Tomcat Connector
The Apache Tomcat Connector (mod_proxy) is a standard component for connecting Apache and Tomcat is usually included in recent Apache distributions. mod_proxy needs to be configured on both the Apache server in the DMZ.
Apache Configuration
The following needs to be added to Apache’s httpd.conf:
Uncomment and edit or add the line in /etc/httpd/conf/httpd.conf for the DMZ tomcat replacing <server_ip_address> with the ip address of the catdv server
<IfModule proxy_wstunnel_module>
ProxyPass /catdv/notifications ws://<catdv_server_ip_address>:8080/catdv/notifications
ProxyPassReverse /catdv/notifications ws://<catdv_server_ip_address>:8080/catdv/notifications
</IfModule>
<IfModule proxy_http_module>
ProxyPass /catdv http://<catdv_server_ip_address>:8080/catdv
ProxyPassReverse /catdv http://<catdv_server_ip_address>:8080/catdv
</IfModule>
This tells Apache to forward all requests to the CatDV web server over ajp13 and tells mod_proxy_ajp the address and port (default 8009) of the CatDV web server.
4. Firewall Rules
How to set firewall rules will be determined by the type and manufacturer of your firewall. However you will need to create a rule to allow TCP traffic, from the Apache server, over port 80 / 443 (or whatever port you choose for your CatDV server) to the CatDV server. Further assistance. Quantum Professional Services can provide technical assistance to set up this kind of deployment via its professional services team. Please visit our “Contact Us” section for further information.
